Millions of Medical Images Exposed, as US Fails to Secure PACS Flaws
A year out from a shocking report that revealed massive PACS vulnerabilities were exposing millions of medical images and data, and NNT shows the US has failed to secure those flaws.

Source: Getty Images
- In the Fall of 2019, a damning report from ProPublica outlined a massive healthcare exposure: millions of medical images generated from Picture Archiving and Communication Systems (PACS) were left exposed and unsecured online. And the US was the biggest culprit.
One year later, and the US healthcare sector has still failed to close these major security gaps, where other countries took action.
The latest data shows that the largest offenders, just eight providers, are leaking more than 4 million medical images and records from about 1 million US citizens. These statistics do not include the remaining 162 healthcare entities that are also exposing this sensitive information.
PACS servers are critical to healthcare infrastructure, as they archive medical images and allow entities to share these records with other providers. But the technology holds several security risks, including the use of DICOM, which has inherent vulnerabilities that could allow an attacker to install malicious code into imaging files to infect patient data.
“Providers work with a lot of referring physicians who may want access to these images, so they will send over the PACS access,” explained Dirk Schrader, Global Vice President at New Net Technologies (NNT). “The same system accessible via the DICOM standard port has a web browser feature that is password protected. But many have overlooked the exposure.”
READ MORE: Sen. Warner Digs into DHA Over Exposed Army Medical Center Images
In fact, Forescout Research Labs ranked PACS among the riskiest devices in the sector. As such, these necessary technologies are also prone to exposures and attacks.
The initial ProPublica report led to a public outcry, followed by an inquiry into one of the biggest exposures caused by TridentUSA. The vendor and its affiliate MobileXUSA failed to secure X-Rays, MRIs, and other health data, while several PACS used by the Army were also found to be exposing data from servicemembers.
Sen. Mark Warner, D-Virginia launched an inquiry into the Department of Health and Human Services, as TridentUSA passed an HHS audit while the PACS exposure was ongoing.
But two months after the report, Greenbone found a 60 percent increase in the number of medical images exposed through vulnerable PACS.
And unsurprisingly, not much has improved in the US a year after the report.
READ MORE: Number of Exposed PACS Medical Images Increasing, US Biggest Culprit
“This vulnerability presents a serious risk to patient data and privacy,” Sen. Warner told HealthITSecurity.com. “I’ve called on the Administration to address this threat, and it’s unfortunate they haven’t fully done that – especially as other nations appear to have gotten it right and threats from nefarious actors against our healthcare infrastructure are only growing.”
The Latest Medical Image Archive Report
NNT research on medical image archives, or what is called PACS, that are connected to the public internet and located in the US, found more than 170 identified systems left completely unprotected.
According to Schrader, 81 of these entities are new from the initial 2019 reports, and 89 are old or previously found by his research. Of the 89 entities, 69 received a responsible disclosure via email in December 2019.
Alarmingly, however, those older systems added 700,000 exams in the last year.
Schrader also found five systems with more than 400,000 exams from an estimated 100,000 patients per each system, in addition to 14 million exams that included patient names, dates of birth, exam dates and descriptions, physician names, patient IDs, institutions, partial SSNs, and more sensitive information,
READ MORE: Most At-Risk Medical Devices: PACS, HL7 Gateway, Radiotherapy Systems
In total, NNT estimates there are about 3.5 million US patients affected by these exposures, including data that goes back to 1989. A majority of these systems are storing data from the last 15 years.
For Schrader, the most concerning finding was SSNs included with COVID-19 diagnoses or HIV-positive information, as well as data from 19 children's hospitals.
The exposures also include several systems leveraging plain web interfaces, connected and unprotected without HTTPS, and using clear text transmission without the need for passwords. These same systems allow files to be uplodaed to the data archives, "possibly to upload infected files."
Another 11 systems allowed a complete, plain-text 114GB data set to be download through HTTP.
Leaving the Door Wide Open
To get a sense of the feasibility and ease in which an hacker could find this data, HealthITSecurity.com spoke extensively with Schrader, a former member of the Greenbone Networks research team responsible for the initial report.
It turns out, the answer is pretty alarming: using legitimate mechanisms given to providers with access to PACS, Schrader easily accessed troves of sensitive information, including HIV statuses, medical images, contact details, and other other health details.
What’s worse, few of these healthcare entities responded to Schrader’s responsible disclosures.
However, the foreign countries found exposing PACS data in the initial report, including Japan, Germany, Brazil, Turkey, and others, all managed to close off these access points to unauthorized access.
The US PACS servers, however, remain unsecured.
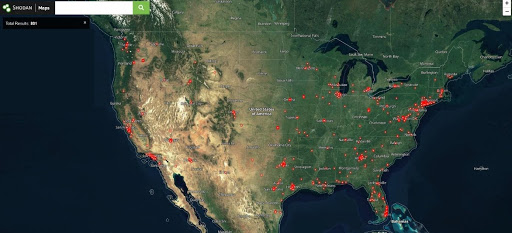
Source: NNT
“What we have found is a long list of unprotected medical systems, especially PACs systems found between the X-Ray machine, CT, MRI scanner, ultrasound machines, image-generating machines, and on the other side, electronic medical records systems and systems to help physicians review images,” Schrader explained.
“They are there to store the images and to be readily available for providers to view because image generation systems are not supposed to store images for a long time,” he added.
The largest exposure was caused by Mendelson Kornblum Orthopedic & Spine Specialists. Schrader found more than 820,000 patient records related to about 8 million images by leveraging SSL certification details and physician names on the system.
Michigan-based Radiology Muskegon was found to be leaking 630,000 exams tied to 4.4 million related images. Though the images were not accessible, Schrader was able to access the patient data.
The third largest exposure was tied to Sutter Buttes Imaging, with 580,000 exams related to 14 million images.
Schrader examined PACS, the DICOM protocol, and other access points to determine just how many systems are connected, as well as how many examinations, systems, and patients are exposed.
The findings are bleak. Schrader expected to find just a small number of unprotected systems in the US, as small clinics or hospitals may not have the necessary cybersecurity resources to address these issues.
But the discovery of 170 health systems leaking patient data, through PACS alone, is not an error, he stressed. All of the discovered healthcare providers were given responsible disclosures, and yet the problem has not improved in the US.
Further, these exposures are not brought on by attacks leveraging brute-force methods or by leveraging user credentials. Schrader stressed that he’s not a hacker, and that he can’t code or script, rather, he’s a security processor. Meaning, finding these images takes little effort or skill.
The issue is that these images are simply left online, through technologies like the DICOM viewer, which can be downloaded from the open internet.
“Using Shodan.io, you can find the IP addresses of these ports, such as the radiology viewer,” he explained. From there, you can use the IP address in combination with the country, state, or city level to find these exposures.
In just a few steps, Schrader gained access to patient names, dates of birth, and patient identification (often similar to a Social Security number). Another quick internet search would allow an attacker to verify whether the ID was a legitimate SSN.
And once an exposed provider is found, an attacker could then combine the IP address with the provider name into Shodan.io to find other infrastructure vulnerabilities.
The data discovered during these simple internet searches can also provide a nefarious actor with enough information to launch social engineering attacks, later leading to fraud, identity theft, and other cybercrimes.
DICOM isn’t the only open port: Schrader found a host of critical vulnerabilities, which show the same providers leaving PACS exposed aren’t monitoring for known security flaws. Many are still exposed to Microsoft vulnerabilities, some disclosed more than five years ago.
NNT found more than 1,600 high severity vulnerabilities across all archive systems connected to the internet, even those with adequate security, as well as about 600 high severity vulnerabilities on 130 unprotected archives, including several with the highest vulnerability ranking.
"Without PACS access, it will impact the business. Why are they leaving it completely unprotected?”
These flaws are easy to address by simply applying the patch provided by the tech company, he added.
Many of these systems show indications of compromise, unknown ports, trojans, and the like, which are typical for victims of trojans. At least one system is suspected to already be compromised.
Schrader also confirmed that the data in these exposures is current and ongoing. During the interview with HealthITSecurity.com, data was updated in near real-time, including data being uploaded from an MRI exam.
As a result, patient data, jail status, health conditions, and other related data were left up for grabs.
“Who is stopping an attacker from uploading malicious files? [The attacker] might get lucky and an employee may click on it, allowing for the installation of a trojan to later deploy ransomware,” Schrader explained.
Recent studies have shown open ports are a key target for ransomware attacks, according to Corvus, which further heightens the need to secure these exposures.
However, these 180 US providers have failed to take up the call to secure these vulnerabilities, which Schrader described as negligence. The providers have failed to respond to responsible disclosures. And none of the providers in question have closed these access points, which are potential HIPAA violations.
Shutting Down Access
Healthcare entities must identify exposures, which are sometimes hidden behind the router or firewall, while security leaders need to verify the organization’s security posture and attack surface.
NNT recommended that organizations leverage HIPAA-required security processes, including risk analysis, risk management, access controls, and safeguards, or audit controls. Healthcare entities must also run vulnerability checks on the attack surface, completely scanning for open ports and unprotected services, particularly from an external point of view.
These leaders can even use Shodan.io to check for their enterprise’s open ports, in the same way an attacker will. For those with minimal security staff or resources, Schrader stressed that there are many free resources available.
Administrators should also monitor and control changes, as when the environment changes, it's important entities understand the consequences.
But at the end of the day, “There’s no magic in it. Use the free tools available, and if an organization sees their enterprise listed, then they will know something is wrong.”
“You don’t have to do it by yourself,” Schrader said. “Make those changes to ensure ports are unreachable from the internet. But also ask yourself, what is the consequence? What do I have to take care of? The problem is that you’re connected to the internet, and attackers are out there searching for you.”
“If you’re not an expert in cybersecurity, that’s okay. But if you don’t take action, there are side effects,” he continued. “What I don’t get here from a process perspective is that these systems correlate to an organization’s business processes. Without PACS access, it will impact the business. Why are they leaving it completely unprotected?”
Forescout recently shared with HealthITSecurity.com some of the biggest issues facing medical device security, which often have similar vulnerabilities to PACS systems, and as such, similar mitigations can be applied.
Entities need visibility into their networks in order map devices and how they communicate, which will provide insights into known security gaps. Segmentation is also crucial, but again, often problematic for providers.
Healthcare organizations should build a foundation of visibility, which will then lead to the segmentation process for both internal and external exposures. Applying zones can also be helpful for those entities continuing to use legacy or vulnerable tech, such as PACS.
