Filling Healthcare Security Staffing Gaps with Virtual CISOs, Students
Over half of organizations still do not have a designated security leader; transitioning internships and virtual CISOs can fill some of those healthcare security staffing gaps.

Source: Getty Images
- In 2017, a damning report from the Department of Health and Human Services Health Care Industry Cybersecurity Task Force revealed the troubled state of healthcare security staffing: three out of four organizations were operating without a designated security person.
That same year saw the emergence of ransomware attacks, which shut down hospital operations and crippled patient care. With the WannaCry and NotPetya attacks, it became very clear that hackers were increasing the sophistication of their attacks and most organizations were not keeping pace.
While awareness has increased tenfold more than two years later, ransomware is still crippling the sector, and the needle has barely moved on the security staffing shortage plaguing all sectors.
As of April 2019, there are more than 313,000 cybersecurity job openings in the US, as calculated between September 2017 and August 2018 by the federal government. And just 4 percent of federal cybersecurity employees are under the age of 30.
In response, President Donald Trump signed an executive order in May 2019 to incentivize and provide guidance for hiring and retaining more security leaders at the federal level.
“The nation is experiencing a shortage of cybersecurity talent and capability, and innovative approaches are required to improve access to training that maximizes individuals’ cybersecurity knowledge, skills, and abilities,” federal officials explained at the time.
“Training opportunities, such as work-based learning, apprenticeships, and blended learning approaches, must be enhanced for both new workforce entrants and those who are advanced in their careers,” they continued.
The staffing shortage has hit the healthcare sector hardest: 79 percent of healthcare organizations find it difficult to recruit security staff, Ponemon reported. And nearly half still don’t have a chief information security officer.
Without a security leader in place, 74 percent of organizations find it’s a serious challenge to maintain effective cybersecurity.
The cybersecurity staffing shortage poses a serious challenge for healthcare organizations. Fortunately, there are several ways to close the gap by taking advantage of educational resources, sharing security leaders, or by hiring a virtual CISO.
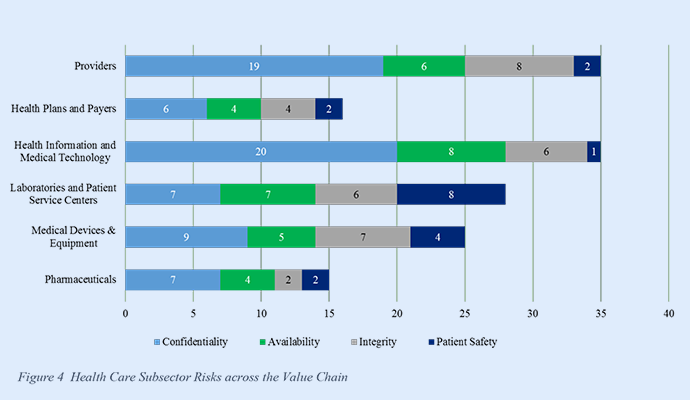
Source: HHS ASPR
Transitioning Staff to Security Roles
More commonly, healthcare delivery organizations will simply transition current in-house staff to security roles when an outside individual can’t be found or afforded. To CynergisTek Executive Advisor Clyde Hewitt, this is rarely a good idea.
“A lot of health organizations aren’t filling staffing gaps effectively,” Hewitt said. “Individuals are being appointed into senior security roles through seniority and longevity, rather than skillset. Unfortunately, for the security career field: it takes a long time to get good at it.”
“And it’s beyond the focus of typical IT,” Hewitt said. “If you look at HIPAA security controls, NIST cybersecurity framework, and other standards, 22 percent of controls are technical, the rest are non-technical. It takes someone well-rounded to understand not only healthcare, but to understand health security and the technical components clearly for it to be done right – especially those IT skills to understand more of the business operation side.”
But can it be done successfully? HSCC believes so, with the right training and qualifications through its in-house IT professionals or clinical engineering staff.
CSSP training is highly affordable, or organizations can look to the healthcare-specific HSCC certification to help transition IT leaders. The process can help those staff members and organizations compare current abilities with well-rounded cybersecurity skills.
HSCC also sees a path to success with transitioning staff if the organization has an internal cybersecurity roadmap for interested employees, develops a mentoring and outreach plan for all capable and interested employees, and considers the development of an internal security internship program, which can help staff understand opportunities within the organization, while helping managers vet interested candidates.
But Melissa Ventrone, a cybersecurity attorney, certified informational privacy professional, and member of Clark Hill, a law firm, voiced concerns with the idea.
“We do see people moved from certain staff positions into security role. But I don’t think that’s the right thing to do,” Ventrone said. “Security is not a hobby: it’s a profession. When you’re taking someone who’s an office manager, their profession is managing an office – not being able to understand the risk from security perspective.”
And the same theory applies to transition physicians to security, as the role requires a specific knowledge base and skillset to perform, explained Shefali Mookencherry, Impact Advisor’s principal advisor. Providers should be limited to an advising role around sharing protected health information or managing patient care and engagement.
To Mookencherry, those considering transitioning staff into security roles should prioritize skills, knowledge, and a willingness to learn over their college degree or initial work experience.
“Some characteristics of a successful cybersecurity professional cannot be learned in a classroom; such as unbridled curiosity, strong ability for problem solving, strong ethics, and an understanding of risks,” Mookencherry explained.
“People with these traits may be able to pick up the technical skills through on-the-job training, industry certifications, pursuing college/online courses, and modern vocational and skills education programs,” she added. “To take it to the next level, I would suggest adding cybersecurity goals and metrics to IT and business leaders in an organization.”
To Ventrone, transitioning staff and providers isn’t the best idea. But training a staff IT leader could potentially be effective as they come into the position after working with the organization and have a general idea of how systems are set up.
Organizations can pull from in-house, which comes with the benefit of the internal capacity and dedication to the organization.
“The risk sometimes is that companies don’t understand the difference between managed services and a security provider: it’s like having an electrical person work on plumbing,” Ventrone said. “They may not be as tied into the security base.”
“Many IT and security people speak different languages, and they may not be able to speak to the board,” she added. “You need broader communication skills, which, surprisingly, is harder to provide.”
Sharing a security leader with another organization is one way to overcome the security staffing challenge, Ventrone said.
Security leaders can also be shared with another organization like a “timeshare CISO,” where the person will share his or her time with another hospital or provider organization. Ventrone explained it can be a viable option, but “only if an organization is successfully filling in those risks.”
“If you’re looking globally, there has to be some resources offered that small organization can tap into,” she added. “Those that have a lean budget, don’t understand there is a need for education first, then resources offered through another organization. But smaller organizations are often missing the boat.”
V-CISOs
Virtual CISOs, or vCISOs, are quickly becoming a sound method for effectively closing security staffing gaps. These cybersecurity leaders are offsite and are commonly shared between several organizations. On the surface, the move could seem risky: the leader is off-site and shares security time with other providers.
Those concerns are valid. But for smaller organizations that may not need a full-time security leader or that may reside in an area where it’s difficult to attract top security talent, a V-CISO can be more than effective at providing the necessary security policies, procedures, and support.
Synoptek, CynnergisTek, Pivot Point Security, Impact Advisors, and a host of others offer these virtual roles, which can be tailored to meet the needs of an organization.
Hospitals often struggle to find and retain security leaders who have the skillset to manage the complexity of the healthcare environment, Hewitt explained. Even with outside recruiting, there’s a moderate amount of movement in CISO roles. Resources also add to the challenge, as many can’t afford to retain top talent. VCISOs can fill that gap, while providing elements a traditional CISO cannot.
“For mid- to small-sized providers, you can clearly see that a vCISO may be an advantage because, number one, they probably can’t afford additional training. But they can take that money and go with a vCISO, which will be shared across two to five hospital districts or providers. There’s an economy of scale.”
“You may be paying more hourly, but you’ll be gaining experience of the vCISO and have the ability to leverage work from all of the other supported organizations. When you obtain a vCISO through a major consulting firm, they have all of the resources behind them from the firm.”
There are many models to the vCISO role, which means a hospital can choose the right option for their needs, whether it’s 20 percent of the vCISO’s time or one day a week. Hewitt explained these roles can either be remote or onsite, as well.
“The vCISO proactively works with operating units and stakeholders to implement practices that meet defined policies and standards for information security,” Mookencherry said. “A key element of the vCISO's role is working with senior staff and management across the organization to determine acceptable levels of risk for the organization and drive security into business processes throughout the organization.”
The role provides a wide range of benefits, such as flexibility, Mookencherry explained. VCISOs can work interim, part-time, or full-time, remotely or on-site, and can be available to come on-site for critical meetings, which is ideal for organizations with an immediate need for cybersecurity resources.
It can also allow an organization to “realize the benefits of an internal information security professional without the added expenses and administrative overhead of hiring and training,” Mookencherry noted.
“A vCISO that is unbiased and independent may be the needed facilitator that can work on controversial issues especially when internal toxic relationships exist within an organization,” she added. “With the guidance of a vCISO, an organization can identify and reduce security risks; can assist with compliance and auditing; and is up to date on privacy and security regulations affecting the organization.”
But, much like with all security, a vCISO is not a silver bullet. Mookencherry explained that organizations will need to still address the security tasks that aren’t part of the contracted vCISO’s responsibilities. It can also be time-consuming to spend time vetting the right vCISO to fill the organization’s needs.
Lastly, building relationships between the vCISO and other within the organization will take a bit more time than compared with onboarding traditional staff.
But for Hewitt, the benefits do outweigh the drawbacks as the vCISO for one organization can provide insights from his security team, including what’s being seen on the threat landscape and recommendations for risk remediation.
“It can more than make up the difference, especially for small hospitals,” Hewitt said. “For large organizations, full-time qualifications are required. And in many cases, it will take several people within the organization working on security; some have more than 20 to 30 security people on staff.”
Contracting Considerations for vCISO Role
Much like with any third-party vendor or business associates, healthcare organizations will need to ensure their contract contains the exact needs of the organizations, expectations, and requirements. But before initiating the process, organizations need to first evaluate their needs.
“You must first document in detail – or at least at some high-level – what it is you need,” Mookencherry said. “This will help you out greatly later on when you look through your notes and the vendor materials and realize that their offerings aren’t the same.”
“When you meet with potential vendors, you need to be able to judge what they can do for you against what you really need them to do and make sure that there’s a good match,” she continued. “Research at least three vendors offering the same services.”
To Hewitt, this should include whether an organization intends to make the vCISO the designated security person for the HIPAA security rule with assigned security responsibility for the organization. Leadership should determine what the scope of their role will be: are they the leader or are they there as support?
For example, sometimes vCISOs are used to do the legwork, but there’s an audit person on board assigned as a full-time employee, such as a chief financial officer or chief information officer. Hewitt stressed that those roles need to be clearly defined and outlined in the contract.
“If there is an incident or event that requires help, do you want the vCISO to reach out and use other resources even if it uses those contracted hours?” Hewitt said. “Even a well-equipped hospital with dozens of people can still struggle [during these events].”
When contracting, organizations need to outline minimum requirements, in terms of experience, Hewitt explained. This includes whether leadership wants the potential vCISO to analyze process or define new policies and procedures. If the vCISO is meant to implement these procedures, the organization might also want to use a security engineer or designer.
Organizations should always ask for references and sample deliverables, and “once you’ve weeded out the vendors who aren’t competitive enough to make it any further, invite the remaining providers in for discussions,” Mookencherry noted.
Much like with any potential employee, all vCISO candidates should be interviewed. Mookencherry explained that organizations should look for knowledge, experience, communication style, and overall fit with the organization.
“Facilitate a final discussion round,” Mookencherry said. “This is the final chance for each of the finalists to make their offer stick and to win your business. Bring them back in separately again and have final discussions about price and your needs from their offerings.”
“Now is when you may want to get even more specific about any special needs your organization has,” she continued. “You’re looking for ways to pick the absolute best vendor, both in terms of price and service, so give them all the information possible for them to sell themselves on or trip themselves up. You’re looking for the differentiators in this step.
College Student Programs
In June 2019, the Healthcare and Public Health Sector Coordinating Council released The Healthcare Industry Cybersecurity Workforce Guide for hiring managers and CISOs. The guide encourages healthcare leaders to consider hiring students, transitioning IT staff to cybersecurity roles, or developing and managing professional development programs for executive-track cybersecurity personnel.
“Attracting and retaining cybersecurity talent is a major challenge in all industry sectors,” Greg Garcia, HSCC executive director for cybersecurity, said at the time. “But as medical and wearable healthcare technology become more connected, patient safety will increasingly rely on cyber safety. A skilled workforce is essential to finding that balance.”
“It’s by advancing this proposition to our cybersecurity professionals – that they are not just technical overhead, but part of the public good of public health and safety – that we can attract the best talent that works in partnership with health practitioners in a clinical environment that understands and invests in the linkage between cyber safety and patient safety,” HSCC stressed.
According to the guide, healthcare organizations can consider hiring college students who can learn cybersecurity skills with part-time work, internships, or externships. In turn, those students can later transition into effective cybersecurity staff, by allowing them to perform work that empowers them to feel like cybersecurity professionals, rather than students.
Several healthcare organizations have already committed to this type of program, where cybersecurity students show up with skills they can immediately put to work within the healthcare organization. Typically, students are highly motivated to do the work, while managers and other staff can help develop their technical and professional skills.
To get the most from the program, organizations will need to develop a student plan that includes:
- Identifying existing functions that could benefit from the program
- Defining processes or tasks that a new resource could implement and formalize
- Evaluating the most frequent event or incident flows able to be documented and taught to the student, who will eventually take over the process.
- Finding the service-level agreements currently missing or not established because of the lack of a dedicated resource
- Creating an itemized checklist of daily, weekly, and monthly compliance and assurance tasks
HSCC found the students best suited for this type of role will have a skillset in business operations, risk, regulatory dynamics, and programming, combined with ethical hacking and site development abilities.
Healthcare delivery organizations can contact local higher education institutions to recruit students and will need to determine whether they’ll provide university credit hours as internship compensation.
Making the Right Choice
Operating without a robust security workforce is risky choice, given that the threats are continuing to become more sophisticated and HIPAA enforcement is not slowing down.
Organizations should invest in exploring whether employing a vCISO or students is a right fit to fill a missing security role, but Mookencherry explained there are some other tactics that can help fill those gaps.
- Re-examine Workforce Strategy: Determine what skills you need today and tomorrow to run a successful security program. Realize that skills and experience can come from a variety of places and adjust your hiring efforts accordingly.
- Improve Engagement and Outreach: Don’t limit outreach to the same old career fairs and recruiting programs. Get involved in community colleges, P-TECH schools, and other educational programs to start building your recruiting base. Reach out to professional organizations and social media websites/companies.
- Robust Support Program for New Hires: Mentorships, rotational assignments, shadowing, and other opportunities help new cybersecurity hires gain experience and learn. Remember, not everyone knows what they want to do right away. Keep new hires engaged by giving them the creative freedom to work on different projects and explore new technologies and services.
- Continuous Learning and Upskilling To retain new talent, keep employees current on the latest skill sets through classes, certifications, and conferences. Cybersecurity is a highly dynamic field, requiring ongoing education and exploration. And be open to employees from other areas of your business who express interest in cybersecurity career paths.
As with any security decision, healthcare leaders will need to first assess current security gaps and other problem areas to ensure they understand the amount of risk and the type of security leader needed to fill those gaps. The right method, whether vCISO, student, or IT staff will be determined by the type of risk, available resources, and availability.
