Increased EHR Adoption Raises Need for Robust Security
Recent cybersecurity attacks on health systems and hospitals shine the light on the importance of EHR security

Source: Thinkstock
- EHR security is one small piece to the larger data security puzzle that healthcare organizations, especially those of a larger size, are becoming increasingly aware of and looking to address.
Under HIPAA, covered entities have the responsibility to ensure that all end-points, including but not limited to mobile devices and connected medical devices, are properly secured so as not to weaken any aspect of the EHR network.
Moreover, healthcare cybersecurity issues are also ever-evolving, and organizations must stay on their toes given the proliferation of online threats. Hacking incidents, ransomware, and phishing scams could all potentially lead to issues in EHR security.
Healthcare is an increasingly attractive target for unauthorized third parties because the data being stored in facilities will lead to much more lucrative gain than financial information alone.
“Web-based EHR systems easily allow them to access data from hundreds or thousands of health networks in one fell swoop,” Digital Guardian Principal Architect of Network and Cloud Security Mark Menke explained in a HealthITSecurity.com contribution piece. “Additionally, like other similar applications, it’s likely that web-based EHR systems suffer from many common vulnerabilities that might give attackers access to backend systems and data – from SQL injections to cross site scripting.”
Menke added that EHR security measures need to be especially vigilant as the Affordable Care Act has created significant incentives for doctors’ offices to embrace EHR systems.
“Most web-based EHR platforms allow physicians to reap the advantages of these efficient tools without needing to invest in hardware, software and IT staff to manage them – which is a big bonus in the healthcare industry, where the margins are small,” he wrote.
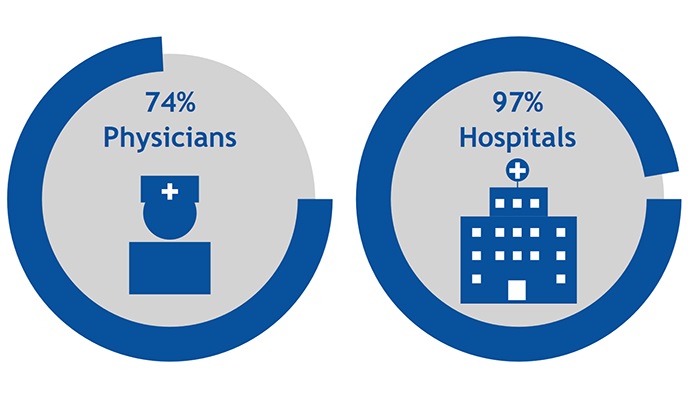
Source: ONC
Collaboration is essential for comprehensive EHR security
Information security is a broad and complex challenge, according to Epic SVP and CSO Stirling Martin. However, the EHR is just one component in a complex ecosystem that also includes securing physical spaces, protecting credentials, networks, biomedical devices, mobile devices and other software.
Martin told HealthITSecurity.com that while HHS lists lost or stolen devices as accounting for many of the breaches, criminal hacking is on the rise.
“Criminal hacking is a profitable, destructive criminal activity,” Martin maintained. “It can also be state-sponsored like the breaches at Anthem and Sony. Can we reasonably expect a healthcare organization to defend itself against another country?”
A provider can no longer be effective against these kinds of attacks in isolation. Instead, Martin explained that security requires “a collaborative, cross-industry safety effort with more cooperation across healthcare and non-healthcare organizations.” This includes vendors, security organizations, and federal agencies, such as the FBI and NSA.
“Today, organizations in healthcare and other sectors are spending millions of dollars to increase their security with surveillance tools, network firewalls, intrusion prevention systems, host level security technologies, multifactor authentication, and integrating commercial threat intelligence. They are also beginning to work together against a common enemy.”
“We get far fewer questions on that, and a lot more questions on whether we have this technology or that technology. My point of view is, that’s probably not the question to be asking.”
Looking toward the rest of 2016 and beyond, it’s important to help healthcare providers by expanding the conversation around security, he urged. This includes looking at “the big picture, facilitate industry collaboration, lobby for reasonable liability caps, and properly label these attacks—crimes by criminals.”
Common healthcare provider concerns with EHR security
While different healthcare providers will often have varied concerns about their EHRs, HIPAA privacy and security concerns are typically a top pain point, according to Chris Haeni, Executive Director of Networking and Security at athenahealth.
Moreover, when athenahealth, which uses cloud-based software, is approached about security concerns, he added that it usually centers around whether the cloud is secure. There is a misconception in health care that only software, which can be installed in an organization’s data center, is secure.
However, if anything has been learned from large breaches, such as that which happened with Target, is that it doesn’t matter what technology an organization is using if it’s not being operated effectively, according to Haeni.
Read: Why a Culture Change is needed for Healthcare Data Security
“We receive far fewer questions on protocols and operating procedures, and a lot more questions on whether we have a specific technology. My point of view is, that’s probably not the question to be asking.”
This is because the majority of healthcare organizations are likely using a compliance-oriented security program, according to Haeni, but they should be using a threat-centric program.
“At the end of the day, security is not a technology problem, it’s a people problem. Organizations should work with technology partners to ensure there are sufficient protocols in place to protect data from specific viable threats.”
Understanding EHR security and ransomware
Ransomware is quickly becoming a more concerning area in the healthcare industry, as more providers have found themselves victims of an attack.
This is a type of malware that usually prevents an organization from accessing certain parts of its system or network. For example, hospital employees could find themselves locked out from critical systems, such as an EHR or patient records. The provider is unable to get in unless they pay a certain amount of money.
There are two main types of ransomware that organizations need to be mindful of: crypto ransomware and locker ransomware. With crypto ransomware, the data is encrypted and made unreadable. With locker ransomware, an organization is locked out of its system and unable to access the data.
Read: Understanding Ransomware and Healthcare Data Security
In one recent case, a hospital was forced to pay $17,000 to regain access to its system. California-based Hollywood Presbyterian Medical Center (HPMC) reportedly fell victim to a malware attack, and employees stated that they were unable to access certain parts of the hospital network.
Just over one month later, Methodist Hospital in Kentucky reported that its servers were infected with the Locky ransomware virus. This particular virus copies all vital files, encrypts them, and then deletes the originals. The hospital’s IT team shut down all of its computers and then verified if they had been affected. Notes were taken by hand during the downtime, according to some employees.
Ransomware attacks can seriously impact an organization’s EHR security. While patient PHI might not be immediately exposed, the information is inaccessible. This could lead to patient safety issues if physicians and nurses cannot see all necessary information to treat an individual.
Or, the PHI could still be viewed by the hackers in question, even if it is not released or exposed to the public.
Protecting against this type of EHR security measure requires healthcare organizations to have a comprehensive data security approach that includes thorough employee training. Oftentimes, malware will infiltrate a system because an employee falls for a phishing scam. Staff members need to know what to look for in suspicious emails and know who to contact if something is found.

Source: Thinkstock
Considering healthcare cloud security options
One of the key things in EHR security options is for healthcare organizations to be confident in the vendor’s ability to keep their data secure. If a health care organization is filling out a questionnaire detailing its own security practices as part of the onboarding process, the vendor should also be able to confidently show how secure its own practices are.
“It’s easy to ask our vendors to do the utmost in security, but it’s very important for health care organizations to routinely audit their own security practices. In security we are only as strong as our weakest link,” he noted. “At athenahealth, we’ve got dedicated security operations teams, dedicated risk teams, and we do threat intelligence sharing with clients.”
However, at the end of the day, both entities must partner together to ensure proper security measures are in place. In the case of a healthcare specific cloud, entities like athenahealth are required by law to be HIPAA compliant, whereas this is not a requirement for software; with software the onus is on the health care system to operate it in a compliant manner.
Because of this, opting for a cloud offering can assist healthcare organizations, because they can share responsibility for all the controls necessary to protect the data, according to Haeni.
“Many health systems are used to managing security on their own, but a cloud provider is also going to be on the hook for security and can become a true partner to help organizations manage risk,” he stated. “That can be an advantage.”
Looking ahead to healthcare data security issues in 2016
Understanding which controls an EHR vendor is going to provide to an organization, and which areas the provider will still have to still operate is one key thing for covered entities to consider as they look for a new EHR security strategy, Haeni explained.
“That needs to be clear and energy should be focused on that. Organizations don’t figure that out probably until it’s too late in the process. They should be really focused on that earlier.”
Haeni also cautioned that it’s important for health systems’ security teams to engage with a vendor before a contract is signed; a covered entity should have its security team on calls early, and involved with contract negotiations.
“[The security solution] may be partially or completely implemented, and only then does the security team start kind of post facto asking questions, such as ‘Oh, what’s this application? What’s this service? Who’s using it? What’s the data?’ And of course that is really ineffective.”
“If you’re an organization with sensitive data, and you’re not backing it up, your endpoints may potentially get infected this way. We see that as a pretty big threat in 2016.”
Looking ahead to the rest of 2016, Haeni said that simple mistakes from insiders will likely be a key issue that healthcare organizations need to keep in mind.
“If you look at the HHS breach data over a long period of time, that’s always been the case,” Haeni warned. “It’s the well-intentioned employee taking that laptop that’s got 500,000 records and forgetting it on the subway, and then those records are considered exposed. That remains a top threat, specifically to healthcare data.”
Ransomware will also likely be a key issue, and is something that athenahealth is watching very closely, he added.
Haeni specifically referenced the crypto locker type of ransomware, where an organization’s information is encrypted. To gain access back, the entity is expected to pay a certain amount of money.
“If you’re an organization with sensitive data, and you’re not backing it up, your endpoints may potentially get infected this way. We see that as a pretty big threat in 2016.”
Finally, third-party security, or supply chain security, is a critical area for the healthcare industry. The current solution is not working very well, according to Haeni.
Read: Using a ‘Layered’ Approach for Health Data Security
“[The current solution] is basically that we create these huge checklists and questionnaires and we send it to our fellow security practitioners at these other organizations and ask them to fill it out,” Haeni explained. “And every single security conference I go to – it doesn’t matter whether you’re providing services or consuming services – everybody seems to understand that it’s not working, but not one knows what else to do.”
While athenahealth goes through extensive third-party reviews, and the company ensures that the organizations it contracts with are also put through the same process, Haeni is not sure the industry as a whole is effective and productive.
Establishing some type of standardization is key, he maintained.
“One of the problems that we face, as a provider [of services], is we try to standardize that information so that we can easily give it to many different parties. Everybody is facing the same challenge of ‘Well, we’ve got to do something, but the tools that we’re using just are not that effective.’”
The questionnaires are often too generic, Haeni added, and the process is not always delivering good outcomes.
“As security practitioners, we’ve got to claw our way out of that problem.”
