How Ransomware Affects Hospital Data Security
Healthcare ransomware is quickly becoming an industry buzzword, but what is it exactly and how can organizations improve their hospital data security?

Source: Thinkstock
- Ransomware is a type of malware that typically prevents organizations from accessing certain parts of its system. For example, an entity and its users could be locked out from critical systems, such as EHRs, and may be unable to get in unless they pay a certain amount of money. This could cause problems for an organization’s hospital data security.
The ransomware will then either deny access to the data or it will encrypt it. The Crypto ransomware will encrypt the data, while locker ransomware prevents users from accessing the information.
It is important to note though, that just because an organization has paid the demanded fee, it is not guaranteed that the data will be made accessible again.
The Institute for Critical Infrastructure Technology (ICIT) called 2016 the year of ransomware, in a report released earlier this year. ICIT added that ransomware will “wreak havoc” on America’s infrastructure.
“Ransomware is less about technological sophistication and more about exploitation of the human element,” ICIT said in its ransomware report. “Simply, it is a digital spin on a centuries old criminal tactic.”
The inability to access critical information “can be catastrophic,” according to the Federal Bureau of Investigation (FBI). Especially “in terms of the loss of sensitive or proprietary information, the disruption to regular operations, financial losses incurred to restore systems and files, and the potential harm to an organization’s reputation.”
Dig Deeper:
- Understanding Ransomware and Healthcare Data Security
- FBI Ransomware Warning Crucial for Healthcare Cybersecurity
How could hospital ransomware attacks affect healthcare?
As previously mentioned, healthcare ransomware attacks could be particularly devastating to a covered entity. With more organizations implementing connected medical devices and creating BYOD strategies or allowing mobile devices to be regularly used, there are more potential access points for unauthorized users.
If a hospital cannot access its own EHR, patient care could be delayed or hindered.
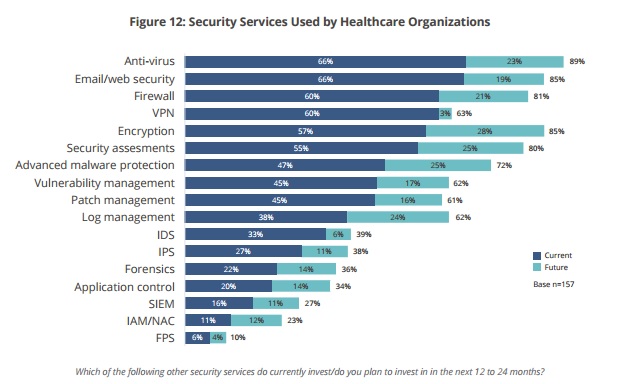
This is why it’s critical for covered entities to implement the necessary security measures, such as advanced malware protection, anti-virus, firewalls, and email/web security.
A recent study found that 89 percent of healthcare organizations either currently have anti-virus, or plan to use it in the future. Furthermore, 85 percent reported that they are currently or soon will be utilizing email/web security.
Source: Peak10
Employee training will also be essential in preventing hospital ransomware attacks. Staff members at all levels need to be able to identify malicious emails, and know when to not click on suspicious links. Reporting the phishing attempts is also important, so an organization can ensure that other individuals do not fall for the same trick.
Ransomware can also infiltrate systems through vulnerable Web servers. It just takes one weak entry point, such as a laptop, desktop computer, or even mobile device. Once exploited, attackers can potentially access an organization’s entire system.
Dig Deeper:
Recent cases of healthcare ransomware attacks
There have been several cases of hospital ransomware attacks in the first half of 2016, with one of the larger cases taking place in California.
Hollywood Presbyterian Medical Center (HPMC) reported in February that it had fallen victim to an attack that encrypted information and prevented staff members from being able to access parts of the hospital network.
HPMC paid $17,000 to regain access, but stated that there was no sign that any information stored on the EHR has been misused or accessed by unauthorized individuals.
Washington, D.C. and Maryland health system MedStar Health reported just one month later that it had also experienced a healthcare ransomware attack. MedStar explained that it shut down its email and EHR systems to ensure that the virus didn’t spread.
Operations across the 10 hospitals in MedStar and its 250 outpatient facilities were halted, and providers reportedly switched to a paper backup system while officials took down all system interfaces on the computer network to prevent virus from spreading further.
San Diego, California-based Alvarado Hospital Medical Center also reported a “malware disruption” in April, but said that its computer systems were recovered without having to pay a ransom.
“The hospital remains fully operational, and no patients have been turned away,” said spokeswoman Laura Gilbert. “All significant clinical systems needed for operations are fully functional. Our I.T. team took great efforts to protect and restore our systems, and a ransom was never paid.”
Dig Deeper:
- More Hospitals Affected by Healthcare Ransomware Attacks
- MedStar Ransomware Attack Caused by Known Security Flaw
What is being done to prevent ransomware attacks?
While hospital ransomware attacks are not a new issue, healthcare is likely becoming a more prominent target because of the sensitive information that organizations in the industry hold.
The apparent increase in healthcare ransomware issues though, has not gone unnoticed, and stakeholders are beginning to take steps to ensure that covered entities and business associates of all sizes have the necessary tools to keep data secure.
For example, the California Senate Public Safety Committee passed ransomware legislation earlier this year that outlaws the online act and specifies how the crime should be prosecuted.
The legislation amends existing law that “establishes various crimes relating to computer services and systems” and defines extortion as “obtaining the property of another, with his or her consent, induced by a wrongful use of force or fear.”
Employee training, strong technology, and comprehensive disaster recovery planning will all be critical tools in preparing for a potential ransomware attack.
Furthermore, SB-1137 defines the introduction of that type of malware on a computer system, computer or data in a computer system, or computer as extortion. Therefore, it will be punishable by imprisonment in a county jail for either two, three, or four years and a fine not exceeding $10,000.
The College of Healthcare Information Management Executives (CHIME) recently called for a more proactive policy management process and maintained that stronger hospital ransomware legislation is necessary to ensure that healthcare organizations can adequately protect against the evolving cybersecurity threat landscape.
CHIME released its statement in conjunction with the Association for Executives in Healthcare Information Security (AEHIS), following a Senate Judiciary Committee Subcommittee on Crime and Terrorism hearing.
The healthcare cybersecurity threats are becoming more sophisticated every day, according to CHIME.
“Even the largest healthcare delivery organizations, with the greatest investment in security programs, may still fall victim to bad actors as we have seen with some of the largest retail organizations, financial institutions and even the federal government suffering large-scale breaches,” the statement read.
Specifically, there must be increased collaboration between device manufacturers and healthcare delivery organizations. FDA approval of high-risk devices should also include “an assurance that the data collected and shared by the device is secure and the device is not an easy entry point to a health system’s network.”
Dig Deeper:
- Preparing for Online Attacks in Hospital Data Security
- How Can Hospital Ransomware Policies Improve in the Industry?
How can covered entities prepare against healthcare ransomware?
As the types of healthcare cybersecurity issues, including ransomware attacks, will likely only continue to evolve along with new technologies, organizations must regularly train employees and update their systems.
Employee training, strong technology, and comprehensive disaster recovery planning will all be critical tools in preparing for a potential ransomware attack, according to Foley & Lardner information security lawyer Mike Overly.
“The recent events in Hollywood and elsewhere have highlighted the problem, but by no means is this necessarily an absolutely new thing in regard to healthcare,” Overly explained. “One of the concerns about ransomware is that unlike an actual data breach, there’s no reporting obligation as to whether or not you’ve been the subject of a ransomware attack.”
Employee education is the first line of defense for any healthcare organization, he added. Covered entities must ensure that the training is appropriate for users who may not necessarily be familiar with technology.
Updated anti-virus software, and other technological tools will also be beneficial. This way, older versions of types of ransomware cannot infiltrate new systems.
Comprehensive and current backup plans are necessary, as this can potentially save an organization from having to shut down entirely.
“It’s those three things that tie together to provide a good defense against ransomware,” Overly stated. “Unfortunately, what we see in many instances, is everyone kind of moves immediately to ‘Oh it just needs a software solution to this.’ Or ‘We need to use better anti virus software and all will be well.’ I think those organizations are not going to serve themselves well with that kind of approach.”
Tenable Strategist Cris Thomas agreed that the benefits of prior planning cannot be underlined enough.
“If you wait until you're attacked or infected with ransomware, and then if you expect to recover quickly, that's not going to work,” he said.
The back up storage should not be connected to the same network, ensuring that the data is not compromised with the main area should an attack occur. Moreover, it will be helpful to know what the initial infection vector was, because if an organization simply restores, the attackers could just regain entry and reinfect the network.
Dig Deeper:
- 5 Healthcare Data Security Challenges and Solutions
- Why Healthcare Network Security Must be a Top Priority
